

An Introduction To SQL Injection


The Internet has never been completely safe ever since its inception. Today we will be talking about one vulnerability that has already victimized Wikipedia and numerous government and e-commerce websites - SQL Injection or SQLi.
A successful SQL Injection attack can not only spoil the reputation of your company and make customers lose trust in you by breaching confidential data but also create false records and modify records to suit ones preferences. You may wonder what will happen if you can only change the account balance against your account number in your bank’s database or increase the number of likes on your social media. If the changes are very subtle it becomes difficult to track and even if the company finds out the vulnerability and fixes it the damage is already done.
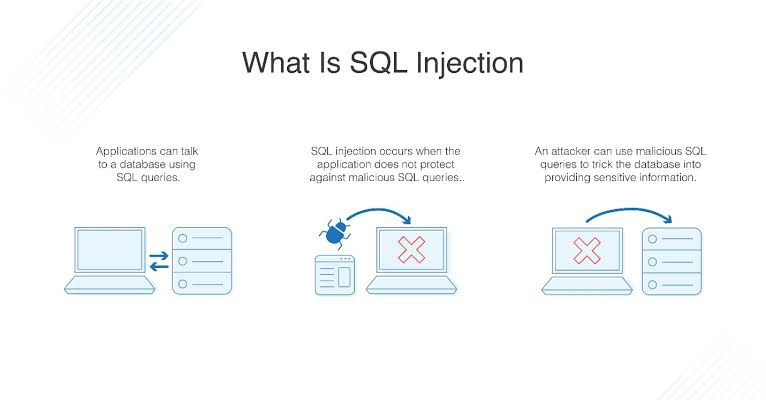
So how does SQL Injection works? Are all the systems vulnerable? The answer is "NO". But once upon a time most of them were and some still are. SQL Injection lets the user run their query on the server DB that is not authorized by the Database Administrator.

SQL Injections can be In-band, Inferential, and out-of-band.
1.In-band SQLi
In In-band SQLi a single channel of communication is used for both launch attacks and gathering results. In-band SQLi’s simplicity and efficiency make it one of the most common types of SQLi attacks. There are two sub-variations of this method:
(I)Error-based SQLi—the attacker intentionally performs actions that cause the database to produce error messages. The attacker can potentially use the data provided by these error messages to gather information about the schema of the database such as fields in a table or table names.
(II) Union-based SQLi—the UNION SQL operator is used to fuse multiple select statements to get a single HTTP response. This response may contain data that can be leveraged by the attacker. In simpler words, one can fetch data from the USER table such as username and password even though the intended SQL works on the Products table.
2.Inferential SQLi
In Inferential SQLi data payloads are sent to the server and the response and behavior of the server is observed to infer its structure. This method is called blind SQLi because the data is not transferred from the website database as a response, thus the attacker cannot see information about the attack in-band. There are two sub-variations of this method:
(I)Boolean—the attacker sends a SQL query to the database prompting the application to return a result. The result will vary depending on whether the query is true or false. Based on the result, the information within the HTTP response will modify or stay unchanged. The attacker can then work out if the message generated a true or false result. If the result is true the query is successfully executed and vice-versa.
(II)Time-based— the attacker sends a SQL query to the database, which makes the database wait (for a period in seconds) before it can react. The attacker can see from the time the database takes to respond, whether a query is true or false. Based on the result, an HTTP response will be generated instantly or after a waiting period. The attacker can thus work out if the message they used returned true or false, without relying on data from the database. If the query takes longer to execute then the query must have executed without any errors.
3.Out-of-band SQLi
The attacker can only carry out this form of attack when certain features are enabled on the database server used by the web application. This form of attack is primarily used as an alternative to the in-band and inferential SQLi techniques.Out-of-band SQLi is performed when the attacker can’t use the same channel to launch the attack and gather information, or when a server is too slow or unstable for these actions to be performed. These techniques count on the capacity of the server to create DNS or HTTP requests to transfer data to an attacker.
To understand how SQL Injection works, let us take the example of a tool shop website. The shop has a huge catalog and hence offers users a search bar to search for the product they are looking for. The website then returns the result and the corresponding price and description. When you enter the search phrase and click on the search button, the text you entered gets sent to the server. The server then creates a SQL Query with that phrase, for example, if you entered hammer a query "SELECT NAME, DESC, PRICE FROM PRODUCTS WHERE NAME = " + search_phrase + ";". This works great as long as the user enters expected phrases for the search_phrase. However, if a user enters something like "HAMMER; DROP PRODUCTS". Instead of one, two queries get executed. The first one is intentional, while the second is secretly injected and deletes the entire table.
There are several ways to prevent SQL Injection attacks:
1. Input Validation: Before running the query, try to find out if the user input contains SQL Elements such as "SELECT" or ";".
2. WAF: Employing a web application firewall takes a lot of responsibility from your shoulder. These firewalls are prepared to check for malicious attacks.
3. Parameterized Statements: Parameterized Statements that work with parameters can be used instead of embedding or joining strings to form a query. A placeholder can only store a value of the given type and not an arbitrary SQL fragment. Hence the SQL injection would only be treated as a strange parameter value.
4. Permissions: By downgrading the permissions for the DB User used by the web application to execute Queries, malicious query execution such as Dropping Tables, or Writing Invalid Data to The rows can be prevented.
credits
www.dnsstuff.com
www.spanning.com
www.portswigger.net
knowledgebooster